Do you need access to a Website on a Protected LAN?
By using the Easy-AD Reverse Forwarding System, Protected Websites and APIs can be made available on the internet.
Enable access to websites on your firewall protected backend. Let Cloud Applications call webhooks that are behind your Corporate or Home Firewalls.
How it works. Use SSH technology to safely get data to those we need it.
Easy Sub-domain Creation
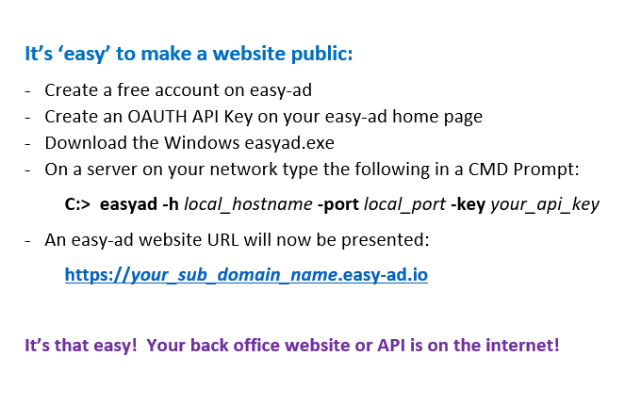
Using the easy-ad dashboard, create a subdomain that you would like to access your Web or API from. If your domain name is MYCOMPANY, create the MYCOMPANY Sub-domain and your api calls will be based on https://MYCOMPANY.easy-ad.io. It is really that easy.
Windows and Unix Services
Download the windows or unix client side HTTP EXE, pass in a few parameters and you have a local website that is now available on the web. Yep, it really is that easy.
No Firewall Rules
With Easy-AD based on SSH port 22, no special requests to your IT department will be necessary. It is really that simple.
Network and Connectivity as Code
First we had infrastructure as code. Programatically turn machines on and off. Why not turn networks that your provide to your customers on and off at scheduled times or based on programatic events. Using the easy-AD Developer API, Create, Enable, Disable or Destroy different network paths that you have provided.

From our blog
Read the articles below to see how our customers use this technology to accomplish data access tasks throughout all phases of a business cylce.
Proof of Concept (POC)
Do you need to allow a customer or testing group to access a website for testing but don't want to give them firewall permissions?
Web API's for All
Exposing an API to your customer/vendor is a very efficient way of keeping the API on your private network but sharing the correct interface the parties that need to verify supply chain, manifest, or environmental data.
Sub Domains with Restricted Hours
The flexibility of Easy-AD allows companies to create different subb-domains for different APIs and Websites. Restricting the hours allows a company to make sure they users access the data during active business hours.


